使用PyCharm打开项目并执行
模块说明
scorer.py
scorer.py:CVS评分模块:支持CVSS、路径长度和中心性指标的加权计算。定义了ContainerVulnerabilityScorer类,通过score方法计算最终评分。
flow_injector.py
flow_injector.py:策略注入模块:调用OpenDaylight控制器接口,实现流量隔离规则的注入。SDNPolicyInjector类提供了inject_block_rule方法,用于下发阻止特定源IP到目标IP流量的规则。
builder.py
builder.py:攻击图建模模块:使用networkx库构建攻击图。该模块定义了AttackGraphBuilder类,提供了添加资产、漏洞、攻击路径等功能,还能获取关键路径和计算节点分数。主要方法如下:
1
2
3
4
5
| add_asset:添加资产到图中。
add_vulnerability:为资产添加漏洞信息。
add_attack_path:添加攻击路径。
get_critical_paths:获取从节点A到节点Z的所有简单路径并排序。
score_node:计算指定节点的漏洞分数。
|
依赖项
requirements.txt文件列出了项目所需的依赖库,目前包含networkx和requests。
安装依赖
在项目根目录下执行以下命令安装依赖networkx和requests库,之后根据实际环境补充资产数据、漏洞分数与控制器信息。
1
| pip install -r requirements.txt
|
控制台输出如下,说明安装成功
1
2
3
4
5
6
7
8
9
10
11
| Collecting networkx (from -r requirements.txt (line 1))
Downloading networkx-3.4.2-py3-none-any.whl.metadata (6.3 kB)
Requirement already satisfied: requests in e:\python\python310\lib\site-packages (from -r requirements.txt (line 2)) (2.31.0)
Requirement already satisfied: charset-normalizer<4,>=2 in e:\python\python310\lib\site-packages (from requests->-r requirements.txt (line 2)) (3.4.0)
Requirement already satisfied: idna<4,>=2.5 in e:\python\python310\lib\site-packages (from requests->-r requirements.txt (line 2)) (3.10)
Requirement already satisfied: urllib3<3,>=1.21.1 in e:\python\python310\lib\site-packages (from requests->-r requirements.txt (line 2)) (2.2.3)
Requirement already satisfied: certifi>=2017.4.17 in e:\python\python310\lib\site-packages (from requests->-r requirements.txt (line 2)) (2024.8.30)
Downloading networkx-3.4.2-py3-none-any.whl (1.7 MB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 1.7/1.7 MB 899.1 kB/s eta 0:00:00
Installing collected packages: networkx
Successfully installed networkx-3.4.2
|
编写测试代码
scorer.py定义了ContainerVulnerabilityScorer类,用于计算漏洞评分,通过如下代码调试
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| from scorer import ContainerVulnerabilityScorer
if __name__ == "__main__":
scorer = ContainerVulnerabilityScorer()
cvss_score = 7.5
path_length = 3
centrality = 0.6
score = scorer.score(cvss_score, path_length, centrality)
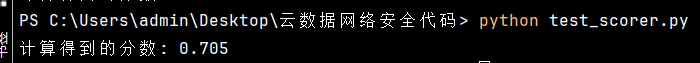
print(f"计算得到的分数: {score}")
|
运行代码,控制台输出
builder.py用于构建攻击图并获取关键路径,通过如下代码调试
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
| from builder import AttackGraphBuilder
if __name__ == "__main__":
builder = AttackGraphBuilder()
builder.add_asset('A', 'Start')
builder.add_asset('B', 'Server')
builder.add_asset('C', 'Database')
builder.add_asset('Z', 'End')
builder.add_vulnerability('A', 'CVE-2025-1234', 7.5)
builder.add_vulnerability('B', 'CVE-2025-5678', 6.0)
builder.add_attack_path('A', 'B', 'Exploit')
builder.add_attack_path('B', 'C', 'Privilege Escalation')
builder.add_attack_path('C', 'Z', 'Data Theft')
builder.build_graph()
critical_paths = builder.get_critical_paths()
print("关键路径:", critical_paths)
|
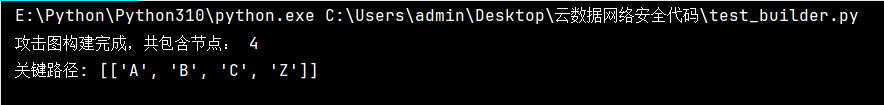
控制台输出
1
2
| 攻击图构建完成,共包含节点: 4
关键路径: [['A', 'B', 'C', 'Z']]
|
flow_injector.py中定义了SDNPolicyInjector类,用于向软件定义网络(SDN)控制器注入流量阻止规则,通过如下代码调试
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| import requests
import json
from flow_injector import SDNPolicyInjector
if __name__ == "__main__":
controller_ip = "your_controller_ip"
switch_id = "your_switch_id"
src_ip = "192.168.1.100"
dst_ip = "192.168.1.101"
injector = SDNPolicyInjector(controller_ip)
injector.inject_block_rule(switch_id, src_ip, dst_ip)
|

